OTAinfo Signup Form
The product consists of 3 parts. OTAinfoSDK, OTAinfoLIB and OTAinfo Cloud.
The product consists of 3 parts. OTAinfoSDK, OTAinfoLIB and OTAinfo Cloud.
Add practice self-assurance in IoT devices. OTAinfo helps in identifying good data and guards device functionality in realtime.

OTAinfo helps
.png)
Our framework help devices establish a clear line between trusted and untrusted data. We do this by defining a “Code of Conduct” for data exchange. All data that reaches the device in any form, by any means and for any use shall follow our “code of conduct” before it is proven to be acceptable.
Data lineage is the log of data flow in your device's supply chain.
With just one line of code, OTAInfo easily integrates with the data transfer locations in your supply chain.
Example OEM has Tier1 supplier which relies on Tier2 supplier for some software piece. The software is passed from Tier2 to Tier1 to OEM. As they are stakeholders in the supply chain, they would generate metadata as the software piece goes up the chain.

.png)
OTAinfo generates metadata from the supply chain, stores it in the OTAinfo cloud and dynamically creates bundles based on IoT device profiles.
Tier2 manufacturers may be working with multiple Tier1 manufacturers who in turn may be supplying the same OEM. A bluetooth chip manufacturer would supply to almost all IoT devices.
Different devices will have different configurations. This means every model of IoT device will be different. OTAinfo cloud tracks all the configurations and dynamically assembles the metadata which is specific to a particular make, model or device.
OTAinfo library describes the device configuration to help get metadata with each piece of data sent from a trusted source. This metadata is validated against data on the device. If the OTAinfo libraries’ code of conduct approves metadata as valid metadata, the data is consumed. User can set the threshold number of signatures to be matched before accepting the data.


IoT devices are in tens of billions. These devices operate in different landscape and are exposed to many kind of contactless digital or other interferences. As a user or provider, an insight to device behavior in receiving data, connections, operative commands, configuration update etc. is most important for a company to succeed in customer satisfaction. A digital twin in the cloud is working in a privileged environment and does not reveal all the information in the device. OTAinfo analytics provides in real time the device performance details.
The card images have fit set to cover, so they fill their masking container without stretching. Try making the “Cards Image Mask” a circle using border-radius or adjusting the size ratio using top padding. Don’t forget to set an alt description for each image, which will help with accessibility.
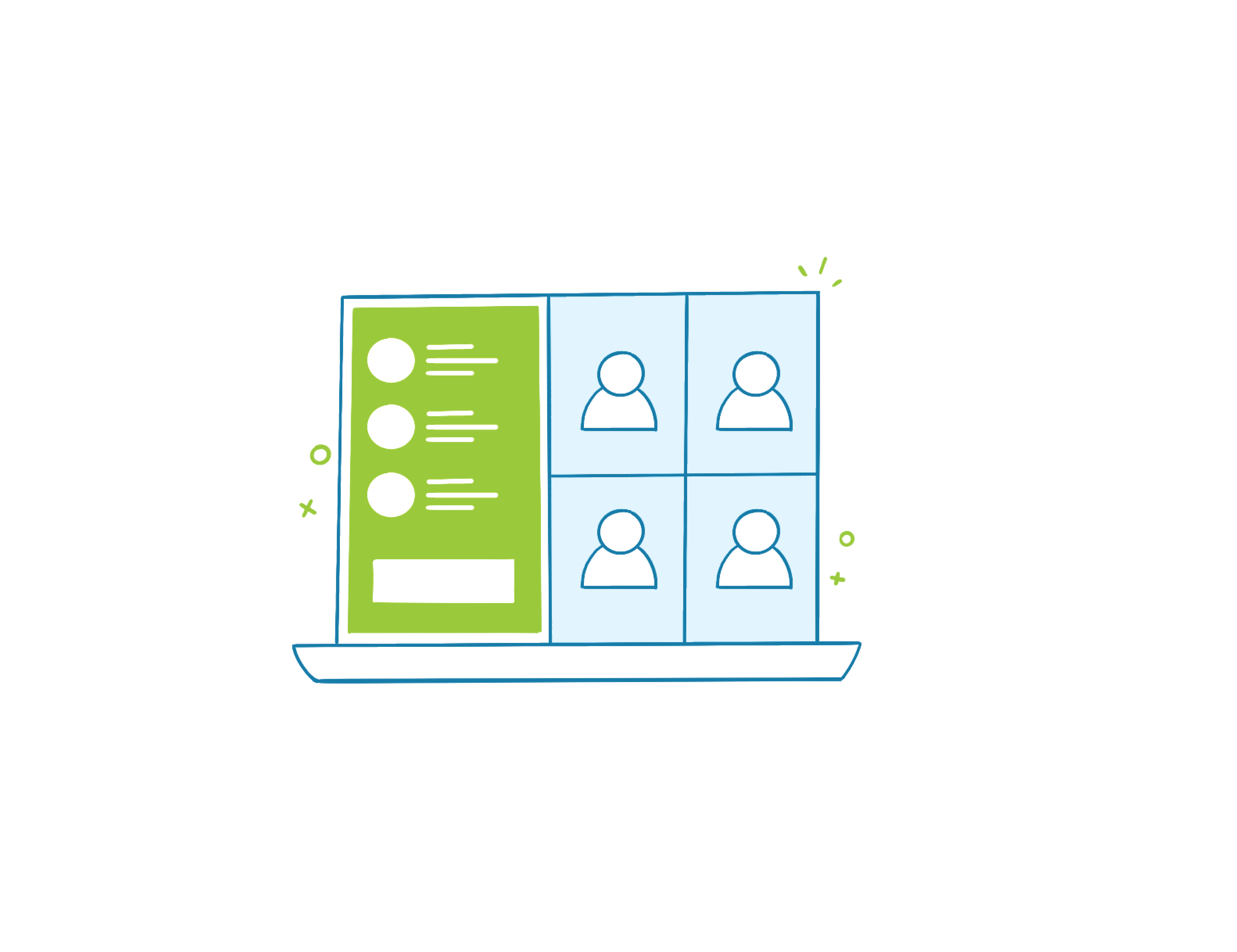
If the meeting details are leaked or a bot application finds out the meeting details which are in progress, it can be hacked. OTAinfo automates verification of guest.
Learn More >>>>

If cellular connectivity is lost, cars cannot be operated. This impacts 1. User experience
2. Car sharing does not have any business if the use is in an area without cellular connectivity. Learn More>>>>

Security is not at every layer but it is decided by IT, clinical engineering and vendors. Hence the main function of the device and the transmission visibility may be overlooked. If these devices do not negotiate trust with the network, user or transmitted line of devices, it can leak data. Learn More>>>>

Devices are subject to Man in the Middle attacks. There are sophisticated software bots/devices which can sense the connectivity options, heat maps or sniff the network data of these devices. The devices are not intelligent enough to defend such attacks or queries from bot/unidentified devices. Learn More >>>>

Send OTA updates with confidence. Automotive industry is moving towards level 5 in autonomous vehicles. In order to maintain its reputation in market, the OEM has not only to distinguish its supply chain protection with uniqueness but also to safeguard the owner of the vehicle. With OTAinfo, add this crown to infrastructure with an affordable overhead. Learn More >>>>